Inside the world of ransomware part 2/3: Different roles within a ransomware attack

Blog
Inside the world of ransomware part 2/3: Different roles within a ransomware attack
Blog written by Noël Keijzer, Cyber security expert at the Northwave CERT
Introduction of the ransomware role model
In our previous blog post we touched upon the structure of a typical ransomware attack, showing how a typical attack consists of three different phases: The IN phase containing all activities aimed at obtaining initial access, the THROUGH phase containing all activities to obtain control over the environment, and the OUT phase consisting of all activities meant to obtain leverage over the victim.
In this blog post we will demonstrate that these activities can be attributed to different roles within a ransomware attack, which are often carried out by different actors. We will shed light on the ways in which the activity in more sophisticated ransomware attacks can be attributed to 7 different roles. And that these each have their own responsibilities in different phases of the attack and are often carried out by different actors. We will start off the blog by describing the Ransomware role model Northwave developed. After that, we will elaborate on why we believe a typical ransomware attack consists of these roles.
The Ransomware role-model
Northwave created this framework based on key insights from dealing with ransomware incidents. As part of our incident response process, we investigate the root cause of such incidents and talk to the actors behind the ransomware attack. From our experiences, we deducted that there are currently 7 distinct roles within a ransomware attack. Each role follows from the objective of the activities that are carried out within the attack. In the past we would see each of these roles fulfilled by the same actor. However, in recent years, we have seen that more and more actors are specialising in a single role within this model.
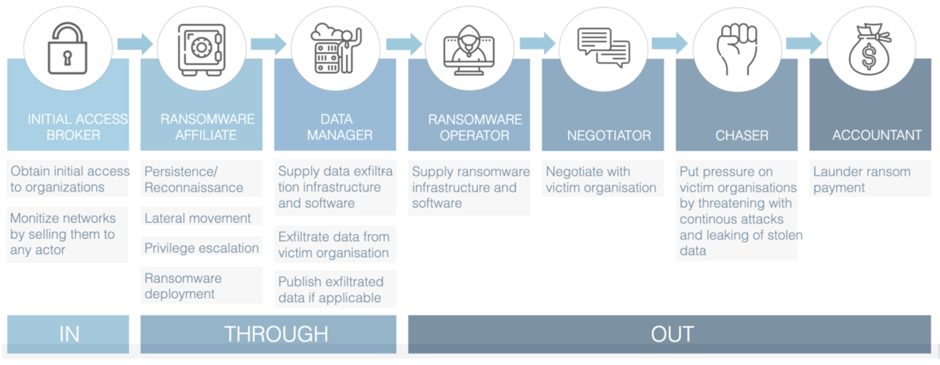
Initial access broker
In most of the ransomware attacks we have investigated, we observed that initial access activity could not be correlated to other activities taking place during the attack. In different attacks where we believe the same actor was fulfilling the ransomware affiliate role, the methods used to obtain initial access to networks were completely different. We also noticed that no activity took place on the network for days or weeks after obtaining initial access to a network. We believe this period of inactivity occurred because the initial access broker was looking for a ransomware affiliate willing to purchase the access to the victim. This is further supported by the fact that there are several criminal groups that specialise in obtaining and selling access to networks. These groups publicly advertise network access on dark net forums. Based on these observations, we believe that all activity surrounding obtaining initial access to victim networks (IN phase) is linked to a separate role, the role of the initial access broker.
Ransomware affiliate
In many of the ransomware attacks we have investigated, we found that the modus operandi for lateral movement and privilege escalation (THROUGH phase) and the ransomware deployment (OUT phase) were identical in attacks involving different initial access methods and different ransomware families. What this indicates is that affiliate activity is performed by the same actor and is not related to a single ransomware family or initial access method. Underground activity shows that most of the large ransomware families currently make use of a “Ransomware-as-a-Service” model. This means that the ransomware affiliates are responsible for deployment of the ransomware within victim networks. Because of this, we believe that all activities surrounding the objective of gaining control over a victim network and deploying ransomware to the network are carried out by a different group of actors, which fulfil the role of ransomware affiliate. We will show in our third blog how we identify threat actors fulfilling the ransomware affiliate role. Additionally, we will show how they can be tracked based on their modus operandi and will show that they work together with different ransomware groups.
Data manager
During conversations with ransomware actors we have, on several occasions, seen chat operators referring to a different party that managed the exfiltrated data when we had questions regarding this. This indicates that a separate actor was managing data exfiltration related matters. During our investigations, we frequently identified traces of activities related to data exfiltration that were taking place in parallel to ransomware affiliate activity (lateral movement and privilege escalation) during attacks. This serves as an indication that a separate actor was performing activities with the objective of exfiltrating data from a victim. Based on these observations, we believe that activities with the objective of exfiltrating data and managing exfiltrated data should be attributed to a separate role, the role of the data manager.
Ransomware operator
As we have already described in the ransomware affiliate role description, we found that the modus operandi of ransomware affiliate activity often is identical for attacks with different ransomware families. A Ransomware-as-a-Service model is also prevalent amongst all large ransomware families. Based on these observations, we believe that all activities related to the objective of facilitating a ransomware business model, think of developing the ransomware and hosting the infrastructure, should be attributed to a separate role, the role of ransomware operator.
Negotiator
From the conversations we have had with ransomware actors, we found that chat operators often have very limited information regarding the ongoing attack they are negotiating the ransom for. Often, they do not even know what victim company they are negotiating with. Furthermore, most of the time the negotiators do not seem to have any knowledge of the means of initial access used to attack the victim, or how attackers managed to further penetrate the network. We noticed that often when we asked for a lower ransom, the negotiators would have to ask permission from their supervisor. This is indicating that they are simply fulfilling a small task within the attack. Some chat operators even failed to notice that another chat operator had already given a discount during earlier conversations. This shows us that the activities related to negotiating with victims are carried out by a separate group of actors. Hence, we believe all negotiation related activity, with the objective of obtaining as high of a ransom payment as possible, should be linked to a separate role within the chain, the Negotiator.
Chaser
A new phenomenon we are starting to observe in attacks is the harassment of victims. The goal of this activity is to put more pressure on them. We observed that critical employees of victim companies would receive calls, where they would be threatened with continuous attacks or publication of the victims’ confidential- or personally identifiable data if they failed to pay the ransom.
Actors fulfilling the role of Chaser would contact key employees of the victim companies in any way possible, calling them, sending them messages on social media, or sending them Emails. All the activity of the actor fulfilling this role had the objective of pressuring victims into paying the ransom. In our experience, these conversations are often scripted and the actor putting pressure on companies has limited knowledge about the incident. They often did not know if negotiations were ongoing, often they were also unaware of which ransomware strain was deployed in the victims’ network. This leads us to believe that these activities were carried out by a separate actor. Therefore, we are under the impression that all activity with the objective of putting additional pressure on the victim to pay the ransom can be linked to a separate role, that of the Chaser.
Accountant
Current arrests being made across the world show that separate actors focus on laundering money for ransomware actors. Examples of this are: the arrest of a Russian national on 12-11-2021 for laundering money for the Ryuk ransomware gang[1] and the arrest of actors linked to the Clop ransomware gang, which are believed to have laundered more than $500M for several cybercrime gangs[2]. We think that all activity related to laundering the ransom money received by the actors should be attributed to a separate role, called the Accountant.
[1] https://www.wsj.com/articles/u-s-accuses-russian-of-money-laundering-for-ryuk-ransomware-gang-11636741333
[2] https://therecord.media/arrested-clop-gang-members-laundered-over-500m-in-ransomware-payments/
Conclusion
To conclude, in this blog, we showed the information we have indicating that the activities occurring during a ransomware incident can be attributed to 7 different roles based on the objective of the activities. Additionally, the information shared in this document gives clear indication of the fact that the current ransomware ecosystem is evolving, and more actors are starting to fulfil separate roles within the ransomware kill chain.
Together with Northwave, the Dutch television programme Nieuwsuur created an in depth video further explaining the ransomware role model, which can be found here.
In part 3, we will track one ransomware affiliate over time and show that collaborations within the criminal ecosystem are very fluid and ever-changing.
